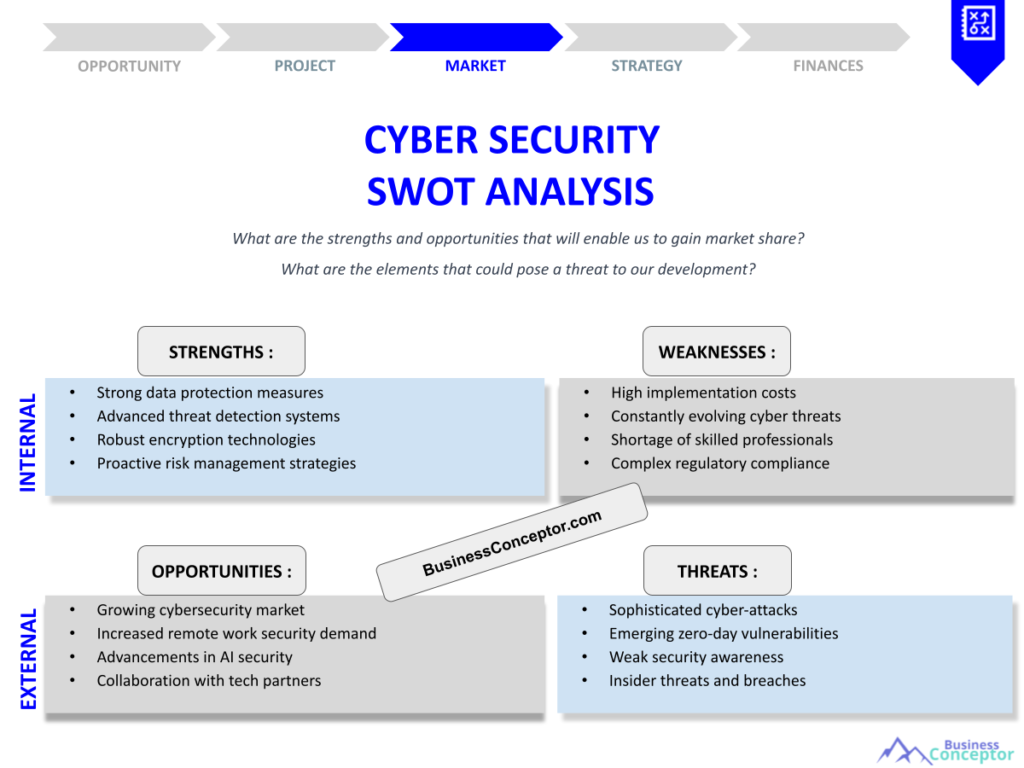
Did you know that nearly 60% of small businesses close within six months of a cyber attack? This shocking statistic highlights the pressing need for robust cyber security measures. Cyber Security SWOT Analysis is a strategic tool that helps organizations identify their strengths, weaknesses, opportunities, and threats related to their cyber security posture. By understanding these elements, businesses can formulate effective strategies to safeguard their digital assets and ensure growth.
- Importance of cyber security in today’s digital age
- Definition of SWOT analysis in the context of cyber security
- Overview of how the analysis can guide strategic planning
- The role of strengths in building a robust security framework
- Recognizing weaknesses to enhance security measures
- Identifying opportunities for improvement and growth
- Understanding external threats and how to combat them
- Real-world examples of successful cyber security strategies
- Best practices for implementing a SWOT analysis
- Future trends in cyber security strategies
Understanding the Basics of Cyber Security SWOT Analysis
Cyber Security SWOT Analysis is more than just a buzzword; it’s a crucial process for organizations looking to enhance their security framework. By breaking down their security landscape into strengths, weaknesses, opportunities, and threats, companies can gain a clearer understanding of where they stand. This analysis serves as a foundation for developing strategic initiatives that can bolster their defenses against cyber threats.
For instance, a company might identify its strength as a highly skilled IT team capable of implementing advanced security measures. Conversely, they may recognize a weakness in outdated software that leaves them vulnerable to attacks. Understanding these dynamics allows organizations to leverage their strengths while addressing their weaknesses head-on.
As we dive deeper into this analysis, it becomes evident how crucial it is for organizations to continually assess their cyber security posture. This ongoing evaluation not only helps in mitigating risks but also positions companies to seize new opportunities in a rapidly evolving digital landscape.
| Strengths | Weaknesses |
|---|---|
| Skilled IT personnel | Outdated software |
| Strong security policies | Lack of employee training |
- Skilled IT personnel
- Strong security policies
- Outdated software
- Lack of employee training
- "The best defense is a good offense." - Unknown
Identifying Strengths and Weaknesses
In any SWOT analysis, understanding strengths and weaknesses is paramount. Strengths refer to the internal capabilities that give an organization an advantage over others. For example, a company with a strong cyber security framework and a dedicated team can respond more effectively to threats.
On the flip side, weaknesses can include anything from inadequate resources to a lack of awareness about potential threats. According to recent studies, organizations that frequently assess their weaknesses are 30% more likely to thwart attacks. This emphasizes the importance of a candid evaluation of internal capabilities.
Recognizing these internal dynamics sets the stage for identifying opportunities for improvement. By focusing on their strengths and addressing weaknesses, organizations can develop a more comprehensive cyber security strategy.
- Conduct an internal audit of existing security measures.
- Identify areas for improvement based on audit results.
- Leverage strengths to enhance overall security posture.
- Regularly assess security protocols to stay ahead.
Exploring Opportunities in Cyber Security
Opportunities in cyber security are often tied to advancements in technology and emerging trends. Organizations can capitalize on these opportunities to enhance their security measures and stay competitive. For instance, adopting AI-driven security tools can significantly improve threat detection and response times.
Statistics show that companies investing in advanced security technologies can reduce breach costs by up to 50%. This highlights the potential for organizations to not only improve their security but also save money in the long run.
As we move forward, it’s essential to explore how these opportunities can be effectively integrated into an organization’s overall strategy. By doing so, companies can position themselves as leaders in cyber security.
- Adoption of AI-driven security tools
- Investment in employee training
- Collaboration with cyber security firms
- "Innovation is the key to staying secure." - Unknown
Assessing External Threats
External threats to cyber security are ever-evolving, making it crucial for organizations to stay informed. From phishing attacks to ransomware, understanding these threats is essential for developing an effective response strategy.
Recent reports indicate that cybercrime is expected to cost businesses over $10 trillion annually by 2025. This staggering figure underscores the urgency of assessing potential threats and preparing accordingly.
By identifying these threats, organizations can tailor their security strategies to mitigate risks effectively. This proactive approach is vital for maintaining a strong security posture.
| Threats | Impact on Organizations |
|---|---|
| Phishing attacks | Data breaches |
| Ransomware | Financial loss |
- Implement regular threat assessments.
- Educate employees on recognizing threats.
- Develop a comprehensive incident response plan.
Developing a Comprehensive Cyber Security Strategy
Creating a robust cyber security strategy involves synthesizing insights from the SWOT analysis. Organizations must prioritize their strengths while addressing weaknesses and preparing for external threats.
For example, a company might focus on enhancing employee training to improve their response to phishing attacks, leveraging their strong IT team to develop effective training programs.
This strategic alignment ensures that organizations are not only prepared for current challenges but also positioned for future growth in a secure manner.
| Elements | Description |
|---|---|
| Employee training | Ongoing education |
| Incident response plan | Preparedness for attacks |
- Align security strategy with business goals.
- Engage all stakeholders in the process.
- Continuously monitor and adapt strategies.
Best Practices for Implementing Cyber Security SWOT Analysis
To successfully implement a Cyber Security SWOT Analysis, organizations should adopt best practices that ensure thorough evaluation and effective strategy formulation. First and foremost, involving key stakeholders from different departments is crucial to ensure a holistic view of the organization’s cyber security posture.
This collaborative approach fosters a culture of security awareness throughout the organization. Regular communication about cyber security measures and ongoing training sessions can empower employees to take an active role in maintaining security protocols.
By adopting these best practices, organizations can create a dynamic cyber security strategy that evolves with changing threats and opportunities. This continuous improvement process is vital for long-term success in safeguarding digital assets.
| Practice | Benefit |
|---|---|
| Involve stakeholders | Holistic evaluation |
| Regular updates | Adaptability to threats |
- Schedule regular SWOT reviews.
- Foster a culture of security awareness.
- Utilize feedback for continuous improvement.
Measuring Success in Cyber Security Initiatives
Measuring the success of cyber security initiatives is vital for understanding the effectiveness of implemented strategies. Organizations should establish key performance indicators (KPIs) to track progress over time. For instance, tracking the number of security incidents before and after implementing new measures can provide valuable insights into the effectiveness of those strategies.
Additionally, organizations can evaluate their response times to threats and the impact of training programs on employee performance. This data-driven approach allows companies to refine their strategies and make informed decisions about future investments in cyber security.
This ongoing evaluation helps organizations refine their strategies and make data-driven decisions to enhance their cyber security posture. By continuously measuring success, businesses can stay ahead of evolving threats and improve their overall security framework.
| KPI | Measurement |
|---|---|
| Number of incidents | Frequency of breaches |
| Response time | Time taken to address threats |
- Define clear KPIs for measurement.
- Regularly review performance data.
- Adjust strategies based on findings.
Future Trends in Cyber Security
The cyber security landscape is constantly evolving, and organizations must stay ahead of emerging trends. By understanding these trends, businesses can proactively adapt their strategies to mitigate risks effectively. One of the most significant trends is the rise of remote work, which has increased the need for secure access solutions. Companies must invest in technologies that facilitate secure remote work environments while ensuring data protection.
Another trend is the growing adoption of AI-driven security tools. These technologies can enhance threat detection and response capabilities, making organizations more resilient against sophisticated cyber attacks. Staying informed about these advancements is essential for maintaining a competitive edge in the digital marketplace.
Organizations that embrace innovation in their cyber security strategies will be better positioned for growth. By integrating new technologies and practices, businesses can not only protect their assets but also enhance their overall operational efficiency.
| Trend | Implication for Security |
|---|---|
| Remote work | Need for secure access |
| AI-driven tools | Enhanced threat detection |
- Stay updated on industry trends.
- Invest in innovative security technologies.
- Adapt strategies to changing landscapes.
Practical Tips for Cyber Security Improvement
Improving cyber security requires actionable steps that organizations can implement immediately. By focusing on practical tips, businesses can enhance their security posture without overwhelming their resources. One effective tip is to conduct regular security audits. These audits can uncover vulnerabilities and ensure compliance with best practices.
Additionally, fostering a culture of security awareness among employees is crucial for preventing human errors. Providing ongoing training and resources can empower staff to recognize potential threats and take appropriate actions.
By following these practical tips, organizations can build a solid foundation for their cyber security initiatives and ensure long-term success. As the digital landscape continues to evolve, being proactive in cyber security measures will be key to safeguarding against future threats.
- "Prevention is better than cure." - Desiderius Erasmus
- Conduct regular security audits.
- Invest in employee training programs.
- Foster a culture of continuous improvement.
Conclusion
In summary, a thorough Cyber Security SWOT Analysis is essential for organizations seeking to strengthen their security measures and foster growth. By understanding their strengths, weaknesses, opportunities, and threats, businesses can develop targeted strategies that not only protect their digital assets but also position them for success in a competitive landscape. Don’t wait until it’s too late! Start your Cyber Security SWOT Analysis today and safeguard your business by exploring our Cyber Security Business Plan Template.
For further insights and guidance on enhancing your cyber security initiatives, check out our articles:
- Cyber Security Profitability: Maximizing Revenue
- Crafting a Business Plan for Your Cyber Security Firm: Step-by-Step Guide
- Crafting a Financial Plan for Your Cyber Security Business: Essential Steps (+ Template)
- Launching a Cyber Security Business: Complete Guide with Example
- Crafting a Marketing Plan for Your Cyber Security Business (+ Example)
- Building a Business Model Canvas for Cyber Security: A Comprehensive Guide
- Customer Segments for Cyber Security Services: Who Are Your Ideal Clients?
- How Much Does It Cost to Start a Cyber Security Business?
- Cyber Security Feasibility Study: Essential Guide
- How to Implement Effective Risk Management for Cyber Security?
- What Are the Steps for a Successful Cyber Security Competition Study?
- How to Address Legal Considerations in Cyber Security?
- What Funding Options Are Available for Cyber Security?
- Cyber Security Growth Strategies: Scaling Success Stories
FAQ Section
What is a Cyber Security SWOT Analysis?
A Cyber Security SWOT Analysis is a strategic tool used to evaluate an organization’s cyber security posture by identifying its strengths, weaknesses, opportunities, and threats.
Why is cyber security important?
Cyber security is crucial for protecting sensitive data and maintaining the integrity of digital systems. It helps organizations avoid costly breaches and enhances trust with clients.
How often should I conduct a SWOT analysis?
It is advisable to conduct a SWOT analysis regularly, at least once a year or whenever significant changes occur in your organization or the cyber threat landscape.
What are common weaknesses in cyber security?
Common weaknesses include outdated software, lack of employee training, and insufficient incident response plans.
How can I identify opportunities in my cyber security strategy?
Stay informed about emerging technologies, trends, and best practices in the cyber security industry to identify potential opportunities.
What are some external threats to cyber security?
External threats can include phishing attacks, ransomware, and various forms of cybercrime.
How can I measure the success of my cyber security initiatives?
Establish key performance indicators (KPIs) and regularly review performance data to gauge the effectiveness of your cyber security initiatives.
What role does employee training play in cyber security?
Employee training is essential for raising awareness and preventing human errors that can lead to security incidents.
What technologies should I invest in for better security?
Consider investing in AI-driven security tools, secure access solutions, and incident response technologies.
How can I create a culture of security awareness?
Foster open communication, provide regular training, and encourage employees to report potential security issues to create a culture of security awareness.