Did you know that cybercrime is predicted to cost the world $10.5 trillion annually by 2025? With such staggering figures, it’s no wonder that businesses are scrambling to fortify their defenses. The Cyber Security Business Model Canvas serves as a strategic framework that helps organizations visualize and structure their approach to cybersecurity. This guide will dive deep into how to create an effective business model canvas tailored specifically for cybersecurity initiatives.
- Importance of cybersecurity in modern business.
- Overview of the Business Model Canvas framework.
- Key components relevant to cybersecurity.
- Steps to build a cybersecurity business model.
- Real-world examples and case studies.
- Common pitfalls and how to avoid them.
- Future trends in cybersecurity business models.
- Recommendations for implementation.
- Tools and resources to assist in the process.
- Final thoughts on cybersecurity as a business imperative.
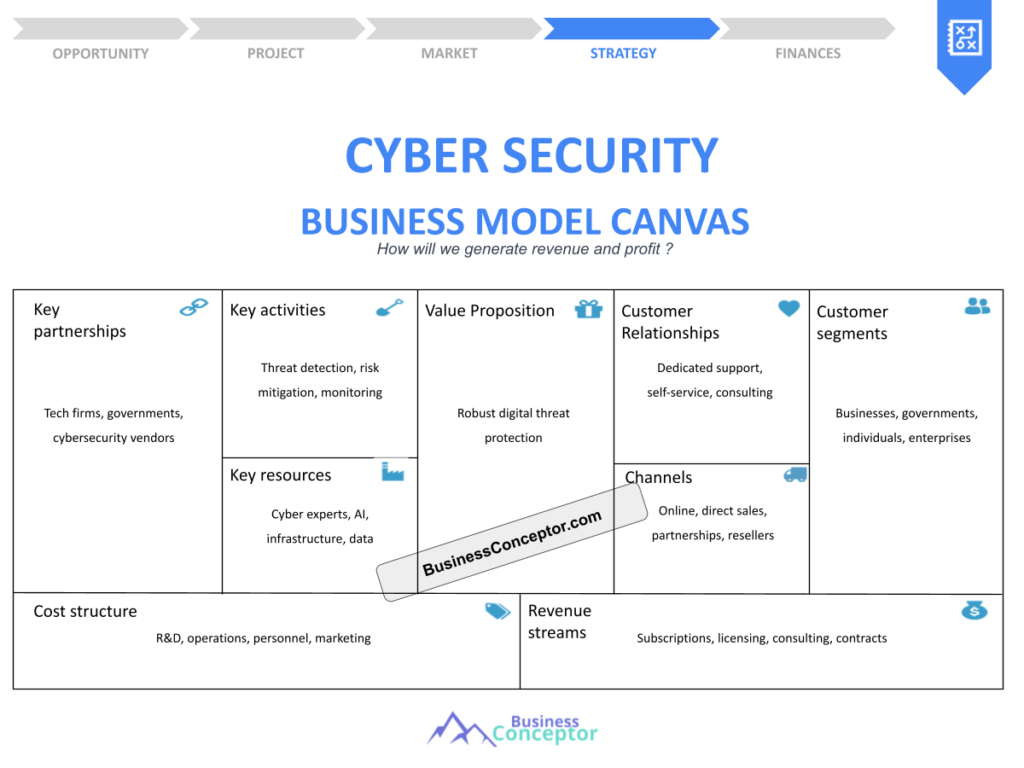
Understanding the Business Model Canvas in Cyber Security
The Business Model Canvas is a strategic tool that allows businesses to map out their value propositions, customer segments, and revenue streams in a structured way. In the context of cybersecurity, this framework can be pivotal in identifying how security measures align with business objectives. By utilizing the Business Model Canvas, organizations can better visualize their approach to cybersecurity and ensure that they are effectively meeting the needs of their customers.
For example, consider a company that provides managed security services. By using the Business Model Canvas, they can clearly define their customer segments, such as small businesses or enterprises, and tailor their services accordingly. This structured approach ensures that cybersecurity solutions are not just reactive but are integrated into the overall business strategy, ultimately driving success and customer satisfaction.
Understanding the components of the Business Model Canvas is essential for creating a robust cybersecurity strategy. As we delve deeper into each section, we’ll explore how to effectively utilize this tool for your organization’s cybersecurity needs.
| Component | Description |
|---|---|
| Value Proposition | What unique value does your service offer? |
| Customer Segments | Who are your target customers? |
| Revenue Streams | How will you generate income? |
| Key Partnerships | Who are your critical partners? |
| Cost Structure | What are the main costs involved? |
- Importance of a structured approach
- Clear identification of customer needs
- Alignment of security measures with business goals
“The best defense is a good offense.”
Crafting Your Value Proposition for Cyber Security
The value proposition is the cornerstone of any business model, and in cybersecurity, it’s even more critical. It defines what makes your security solutions unique and why customers should choose you over competitors. A well-crafted value proposition not only highlights your strengths but also resonates with your target audience’s needs and concerns.
For instance, if your company specializes in advanced threat detection, your value proposition might emphasize real-time monitoring and proactive threat mitigation. Statistics show that businesses with strong value propositions see a 40% increase in customer retention, highlighting the importance of this element. By clearly articulating the benefits of your offerings, you can differentiate yourself in a crowded market.
Once you’ve crafted a compelling value proposition, it sets the stage for the rest of the business model canvas. The next step will be to identify the customer segments that will benefit most from your offering, ensuring that your messaging aligns with their specific needs.
- Identify your unique selling points.
- Research competitor offerings.
- Tailor your message to resonate with your target audience.
- The above steps must be followed rigorously for optimal success.
Identifying Customer Segments in Cyber Security
Customer segmentation is crucial for tailoring your cybersecurity offerings. Different organizations have varying security needs based on their size, industry, and threat landscape. By understanding these differences, you can create targeted marketing strategies and service offerings that speak directly to your customers’ needs.
For example, a small e-commerce site may prioritize data protection, while a healthcare provider may focus on regulatory compliance. Understanding these distinctions allows you to effectively segment your market and tailor your services accordingly. This strategic approach not only enhances customer satisfaction but also fosters long-term loyalty.
Once you’ve identified your customer segments, the next step is to outline the revenue streams that will sustain your cybersecurity business model. Recognizing how to monetize your offerings effectively is key to ensuring the viability of your operations.
- Segment customers based on industry
- Prioritize based on security needs
- Tailor services to each segment
“Know your customer, know your business.”
Exploring Revenue Streams for Cyber Security Services
Revenue streams are the lifeblood of any business, including cybersecurity. Identifying how your services will generate income is essential for sustainability. A well-defined revenue model not only helps in forecasting financial performance but also aids in strategic planning.
Common revenue models in cybersecurity include subscription-based services, one-time consulting fees, and incident response retainers. According to industry reports, subscription models are increasingly popular, with businesses preferring predictable costs over variable expenses. This trend indicates that clients value ongoing support and services that adapt to their changing security needs.
After establishing your revenue streams, it’s important to analyze the cost structure to ensure profitability. Understanding the relationship between costs and revenues will allow you to make informed decisions about pricing and service offerings, ensuring your cybersecurity business model remains viable in the long run.
| Revenue Model | Description |
|---|---|
| Subscription | Recurring monthly or annual fees for ongoing services |
| Consulting | One-time fees for specific security assessments or solutions |
| Retainers | Ongoing fees for incident response and support services |
- Assess market demand for services
- Explore different pricing strategies
- Consider bundled service offerings
“Success in business requires a solid financial foundation.”
Key Partnerships in Cyber Security
Establishing key partnerships is vital for enhancing your cybersecurity business model. Collaborating with other organizations can provide additional resources and expertise that can strengthen your service offerings. This is particularly important in a field as dynamic as cybersecurity, where staying ahead of threats requires constant innovation.
For example, partnerships with technology vendors can allow access to advanced tools and solutions that can enhance your service offerings. Additionally, teaming up with other cybersecurity firms can help expand your reach and share knowledge. These collaborations can lead to improved service delivery, greater customer satisfaction, and ultimately, higher revenues.
Understanding your key partnerships will also inform your cost structure and help identify potential areas for investment. By leveraging partnerships effectively, you can optimize your operations and create a more resilient cybersecurity business model.
| Partnership Type | Benefit |
|---|---|
| Technology Vendors | Access to advanced tools and resources |
| Industry Associations | Networking and knowledge sharing opportunities |
- Identify potential partners in your industry
- Evaluate the benefits of each partnership
- Foster relationships with key stakeholders
“Collaboration is key to overcoming cybersecurity challenges.”
Analyzing Cost Structure for Cyber Security
The cost structure outlines all the expenses associated with running your cybersecurity business. Understanding your costs is critical for pricing your services appropriately and ensuring overall profitability. A well-defined cost structure allows you to identify where you can optimize expenses and allocate resources effectively.
Key expenses may include technology investments, staff salaries, training programs, and compliance costs. A detailed analysis can help identify areas where costs can be minimized without sacrificing service quality. For example, investing in automation tools can reduce the need for manual processes, ultimately leading to cost savings and increased efficiency.
Once you have a clear picture of your cost structure, you can make informed decisions regarding pricing and investment in growth opportunities. This understanding will also aid in evaluating the sustainability of your cybersecurity business model in the long run.
| Cost Category | Description |
|---|---|
| Personnel | Salaries and training costs for your team |
| Technology | Software, hardware, and licenses needed for operations |
| Compliance | Costs associated with regulatory adherence |
- Regularly review and update your cost structure
- Consider cost-effective solutions
- Budget for unexpected expenses
“A strong foundation in cost management leads to business success.”
Future Trends in Cyber Security Business Models
The cybersecurity landscape is constantly evolving, and so should your business model. Staying ahead of trends is essential for long-term success. As threats become more sophisticated, businesses must adapt their strategies to address new challenges effectively.
Emerging technologies, such as AI and machine learning, are transforming the way cybersecurity services are delivered. Companies that adopt these technologies can offer more efficient and effective solutions, giving them a competitive edge. For instance, AI-driven threat detection can significantly enhance response times and reduce the likelihood of breaches.
As you look to the future, consider how these trends can be integrated into your business model to ensure ongoing relevance and profitability. Embracing innovation will not only improve your service offerings but also position your cybersecurity business as a leader in the industry.
| Trend | Impact on Cyber Security |
|---|---|
| AI and Machine Learning | Enhanced threat detection and response capabilities |
| Zero Trust Security | More rigorous access controls to protect sensitive data |
- Keep an eye on technological advancements
- Invest in training for new tools
- Adapt your model to changing market demands
“Innovation is the key to staying ahead in cybersecurity.”
Implementing the Cyber Security Business Model Canvas
Now that you have a comprehensive understanding of the various components of the Business Model Canvas, it’s time to implement your strategy. The successful execution of your cybersecurity business model requires careful planning and collaboration across your organization.
Start by assembling a cross-functional team to ensure that all perspectives are considered. This team should include individuals from IT, operations, and marketing to create a holistic approach to your cybersecurity initiatives. Regular meetings can help keep everyone aligned and focused on common goals, fostering a sense of shared responsibility for the business model’s success.
As you implement your model, be open to feedback and ready to pivot as necessary. Continuous improvement is key in the ever-changing field of cybersecurity. By regularly evaluating your strategies and adjusting based on performance metrics, you can ensure that your cybersecurity business model remains effective and relevant.
| Step | Action |
|---|---|
| Assemble a team | Gather diverse perspectives from different departments |
| Define goals | Set clear, measurable objectives for your cybersecurity strategy |
| Monitor progress | Regularly review and adjust plans based on outcomes |
- Foster a culture of collaboration
- Use feedback to refine your approach
- Stay agile and ready to adapt
“Effective implementation is the bridge between strategy and success.”
Practical Tips for Success in Cyber Security Business Models
To wrap up, let’s discuss some practical tips that can help you succeed in implementing your cybersecurity business model. These actionable insights will guide you as you navigate the complexities of the cybersecurity landscape.
First, focus on building strong relationships with your customers. Regular communication and feedback loops can enhance customer satisfaction and loyalty, which are vital in a competitive landscape. Make it a priority to understand their evolving needs and tailor your services accordingly.
Additionally, invest in ongoing education for your team. Cybersecurity is a field that requires constant learning, and keeping your staff updated on the latest trends and threats will pay off in the long run. Consider offering training sessions, workshops, or access to online courses to empower your team.
“Success comes to those who persevere.”
- Engage with your customers regularly
- Provide training and development opportunities
- Stay informed about industry trends
Conclusion
In conclusion, building a Cyber Security Business Model Canvas is an essential step for any organization looking to enhance its cybersecurity posture. By following the steps outlined in this guide, you can create a comprehensive strategy that aligns with your business objectives and addresses the evolving threat landscape. To assist you further, consider utilizing our Cyber Security Business Plan Template to streamline your planning process.
Additionally, we invite you to explore our other articles on cybersecurity that can provide valuable insights:
- SWOT Analysis for Cyber Security: Strategies for Growth
- Cyber Security Profitability: Maximizing Revenue
- Crafting a Business Plan for Your Cyber Security Firm: Step-by-Step Guide
- Crafting a Financial Plan for Your Cyber Security Business: Essential Steps (+ Template)
- Launching a Cyber Security Business: Complete Guide with Example
- Crafting a Marketing Plan for Your Cyber Security Business (+ Example)
- Customer Segments for Cyber Security Services: Who Are Your Ideal Clients?
- How Much Does It Cost to Start a Cyber Security Business?
- Cyber Security Feasibility Study: Essential Guide
- How to Implement Effective Risk Management for Cyber Security?
- What Are the Steps for a Successful Cyber Security Competition Study?
- How to Address Legal Considerations in Cyber Security?
- What Funding Options Are Available for Cyber Security?
- Cyber Security Growth Strategies: Scaling Success Stories
FAQ Section
What is a Cyber Security Business Model Canvas?
A Cyber Security Business Model Canvas is a strategic tool that helps organizations outline their cybersecurity strategies, including value propositions, customer segments, and revenue streams.
Why is a value proposition important in cybersecurity?
A strong value proposition helps differentiate your services and attract customers by clearly articulating the unique benefits of your cybersecurity solutions.
How can I identify my customer segments in cybersecurity?
Analyze your target market based on industry needs, company size, and specific security challenges to effectively tailor your offerings.
What are common revenue streams in cybersecurity?
Common revenue streams include subscription services, consulting fees, and incident response retainers.
How can partnerships enhance my cybersecurity business model?
Collaborating with technology vendors and other cybersecurity firms can provide access to resources and expertise that enhance your service offerings.
What should I include in my cost structure?
Your cost structure should include personnel costs, technology investments, and compliance-related expenses.
How do emerging technologies impact cybersecurity business models?
Technologies like AI and machine learning can improve threat detection and response, allowing businesses to offer more efficient services.
What steps should I take to implement my cybersecurity business model?
Assemble a cross-functional team, define clear goals, and monitor progress regularly to ensure successful implementation.
How can I ensure my cybersecurity team stays up-to-date?
Invest in ongoing training and encourage a culture of continuous learning to keep your team informed about the latest trends and threats.
What are some practical tips for success in cybersecurity?
Engage regularly with customers, invest in team education, and stay informed about industry trends to ensure success in your cybersecurity initiatives.