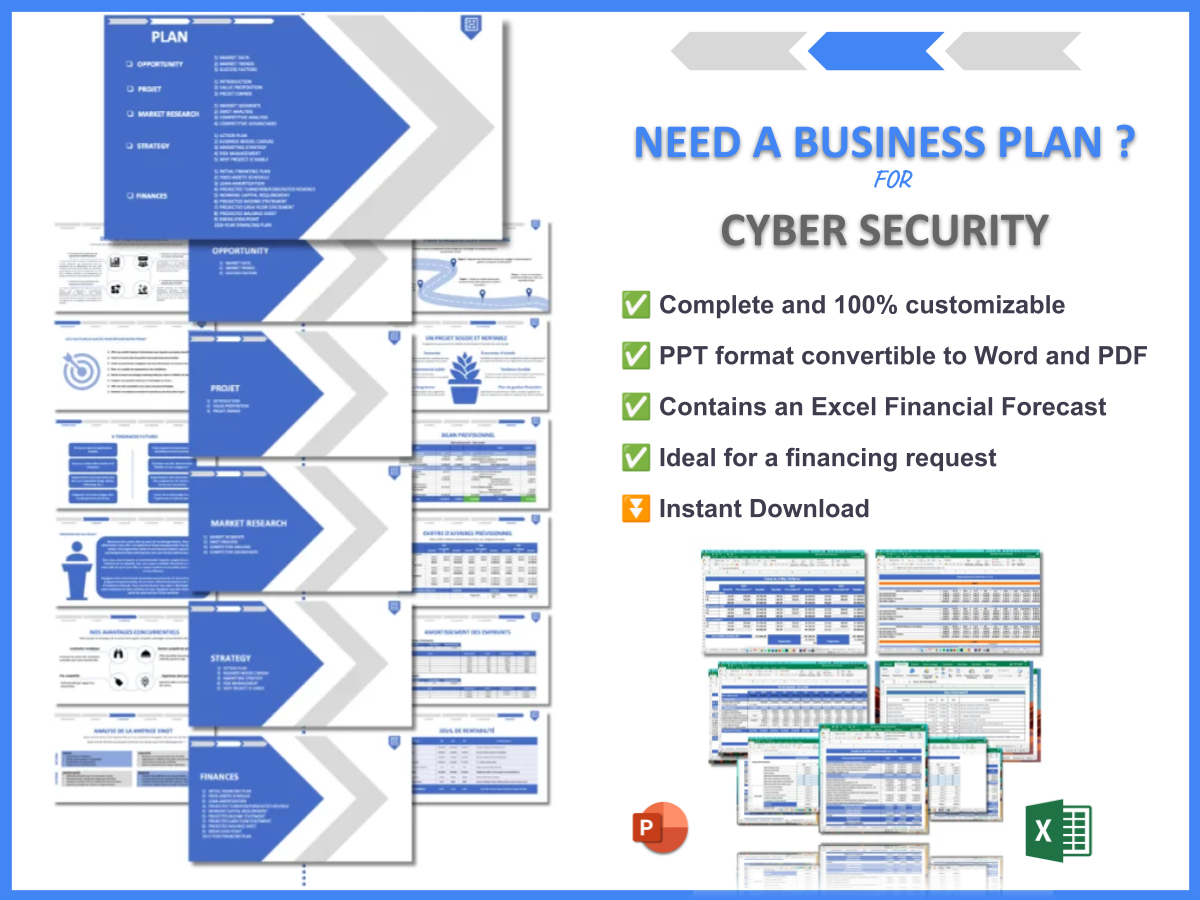
Did you know that over 90% of companies experience some form of cyber attack each year? That’s a staggering statistic that emphasizes the importance of safeguarding your digital assets. In this Cyber Security Feasibility Study, we’ll explore how organizations can assess their security needs and develop effective strategies to mitigate risks. A feasibility study in cyber security is essentially an evaluation of the potential risks and benefits of implementing security measures, ensuring that businesses can protect their sensitive information and maintain trust with their clients.
- Understanding the importance of a cyber security feasibility study.
- Key components to include in your study.
- Steps to identify potential risks.
- Importance of stakeholder engagement.
- Evaluating technology solutions for security.
- Analyzing costs versus benefits of security measures.
- Developing a robust incident response plan.
- Ensuring compliance with regulations.
- Real-world examples of successful studies.
- Future trends in cyber security feasibility studies.
Understanding Cyber Security Feasibility Studies
A cyber security feasibility study is a comprehensive assessment that determines the viability of implementing security measures within an organization. It identifies potential vulnerabilities and assesses the current security landscape, helping businesses understand their risk exposure. This initial step is crucial for developing an effective cyber security strategy that aligns with organizational goals and resources.
For instance, consider a mid-sized company that recently experienced a data breach. By conducting a feasibility study, they were able to identify the root causes of the breach, such as outdated software and insufficient employee training. This study not only highlighted the vulnerabilities but also provided actionable recommendations for improving their security posture, including investing in updated technology and implementing regular training sessions for employees.
Ultimately, understanding the significance of a cyber security feasibility study sets the foundation for a proactive approach to risk management. In the next section, we will delve into the key components that should be included in every feasibility study.
| Key Element | Description |
|---|---|
| Risk Assessment | Identifying potential vulnerabilities |
| Technology Evaluation | Analyzing current security solutions |
| Cost-Benefit Analysis | Weighing costs against potential losses |
| Stakeholder Engagement | Involving key personnel in decision-making |
- Importance of risk assessment
- Evaluating existing technology
- Engaging stakeholders…
“Cyber security is not a product, but a process.” – Bruce Schneier
Key Components of a Cyber Security Feasibility Study
To create a thorough cyber security feasibility study, several key components must be addressed. First, conducting a detailed risk assessment is vital. This involves identifying the critical assets that require protection, assessing potential threats, and evaluating the impact of those threats on the organization.
For example, a financial institution might face risks such as data breaches, insider threats, or ransomware attacks. By quantifying these risks and their potential impact on operations and reputation, the institution can prioritize its security initiatives effectively. Furthermore, utilizing statistical data can bolster the findings of the study, showcasing trends in cyber threats and their implications for similar organizations.
By clearly outlining these key components, organizations can ensure a comprehensive approach to their feasibility study. The next section will discuss the importance of stakeholder engagement in this process and how it can enhance the study’s effectiveness.
- Conduct a risk assessment
- Evaluate current security technology
- Engage stakeholders for input
- Analyze costs versus potential losses
– The above steps must be followed rigorously for optimal success.
Engaging Stakeholders in the Feasibility Study
Engaging stakeholders is a critical aspect of a cyber security feasibility study. Involving individuals from various departments ensures a holistic view of the organization’s security needs. Stakeholders can provide valuable insights into potential risks and existing security gaps that might not be apparent from a technical perspective alone.
For instance, during a feasibility study at a healthcare organization, input from clinical staff revealed that certain patient management systems were particularly vulnerable due to outdated software. By incorporating this feedback, the organization was able to prioritize updates for these systems, significantly reducing their risk exposure.
Engaging stakeholders not only enriches the study but also fosters a culture of security awareness within the organization. This collaborative approach lays the groundwork for effective implementation of security measures, which we will explore in the next section.
- Importance of cross-departmental collaboration
- Gathering diverse perspectives
- Fostering a culture of security…
“Collaboration is the key to success.” – Anonymous
Evaluating Technology Solutions for Security
An essential part of a cyber security feasibility study is evaluating the technology solutions available for securing an organization’s assets. This involves researching various security tools and determining which ones align with the organization’s specific needs and budget.
For example, a company may consider implementing a multi-factor authentication system to enhance access controls. By comparing different vendors and understanding the features and costs associated with each option, the organization can make an informed decision that balances security needs with budget constraints.
By thoroughly evaluating technology solutions, organizations can ensure they invest in tools that not only address current vulnerabilities but also adapt to evolving cyber threats. The next section will discuss the financial aspects of the feasibility study, including cost-benefit analysis.
| Solution Type | Pros |
|---|---|
| Multi-Factor Authentication | Enhanced security for user access |
| Endpoint Protection | Protects devices from malware attacks |
| Security Information and Event Management (SIEM) | Centralized monitoring and incident response |
- Research security solutions
- Compare vendors
- Assess long-term costs and benefits
– The above steps must be followed rigorously for optimal success.
Cost-Benefit Analysis in Cyber Security Feasibility Studies
Conducting a cost-benefit analysis is crucial for determining the financial viability of proposed cyber security measures. This analysis helps organizations weigh the potential costs of implementing security solutions against the financial impact of possible security breaches.
For instance, a company might estimate that implementing a new firewall system would cost $50,000, while the potential losses from a data breach could reach $1 million. By presenting this data clearly, decision-makers can justify the investment in security measures to stakeholders.
Ultimately, a well-executed cost-benefit analysis not only highlights the financial implications of security investments but also underscores the importance of prioritizing cyber security. The next section will address the necessity of developing a robust incident response plan.
| Investment | Estimated Cost | Potential Losses from Breach |
|---|---|---|
| New Firewall | $50,000 | $1,000,000 |
| Employee Training Program | $20,000 | $500,000 |
- Estimate costs of security measures
- Assess potential financial losses
- Make informed decisions…
Developing a Robust Incident Response Plan
A vital component of any cyber security feasibility study is the development of a robust incident response plan. This plan outlines the steps an organization should take in the event of a security breach, ensuring that employees know how to react quickly and effectively.
For example, a retail company may face a data breach during a holiday shopping season. By having a well-defined incident response plan, the company can mitigate damage, communicate with affected customers, and restore operations more efficiently than if they had no plan in place.
Crafting a detailed incident response plan not only prepares organizations for potential threats but also builds confidence among stakeholders. The next section will discuss compliance requirements and how they impact the feasibility study.
| Component | Description |
|---|---|
| Detection | Identifying the breach |
| Containment | Limiting the impact of the breach |
| Communication | Informing stakeholders and customers |
- Identify potential incidents
- Outline response steps
- Review and update the plan regularly
– The above steps must be followed rigorously for optimal success.
Compliance Requirements in Cyber Security
Compliance with industry regulations is another critical aspect of a cyber security feasibility study. Organizations must be aware of the legal and regulatory frameworks that govern their operations, as non-compliance can result in severe penalties.
For instance, organizations in the healthcare sector must comply with HIPAA regulations, which mandate strict data protection measures. A feasibility study should evaluate the organization’s current compliance status and identify areas for improvement to avoid costly fines.
By incorporating compliance requirements into the feasibility study, organizations can ensure they meet legal obligations while also enhancing their overall security posture. The next section will provide additional details about the critical aspects of the feasibility study.
| Regulation | Industry |
|---|---|
| HIPAA | Healthcare |
| PCI-DSS | Payment Card Industry |
| GDPR | Data protection in the EU |
- Identify relevant regulations
- Assess compliance status
- Implement necessary changes…
Final Considerations for Cyber Security Feasibility Studies
When conducting a cyber security feasibility study, it’s essential to consider the ongoing nature of cyber threats. Organizations must remain vigilant and adapt their security strategies to address emerging risks continually.
Additionally, regular reviews of the feasibility study are crucial to ensure that security measures remain effective and relevant. This proactive approach helps organizations stay ahead of potential threats and minimizes vulnerabilities.
By incorporating these final considerations, organizations can ensure their feasibility study provides a solid foundation for ongoing security efforts. The next section will summarize the key actions and recommendations for implementing a successful cyber security feasibility study.
| Consideration | Description |
|---|---|
| Regular Reviews | Continually assess security measures |
| Employee Training | Keep staff informed about security |
| Update Incident Plans | Ensure response plans remain effective |
- Review security measures regularly
- Train employees continuously
- Update incident response plans
– The above steps must be followed rigorously for optimal success.
Key Actions and Recommendations
As we conclude our exploration of cyber security feasibility studies, it’s essential to highlight the key actions and recommendations for organizations. By following these guidelines, businesses can create a robust security framework that protects their assets and reputation.
For instance, conducting regular security assessments and engaging stakeholders can significantly enhance an organization’s security posture. Additionally, investing in employee training ensures that all personnel are aware of potential threats and know how to respond appropriately.
By taking these actions, organizations can build a resilient cyber security strategy that not only protects against current threats but also prepares for future challenges.
“Success comes to those who persevere.”
- Conduct regular risk assessments
- Engage stakeholders throughout the process
- Invest in technology solutions…
Conclusion
In summary, a cyber security feasibility study is an essential tool for organizations looking to safeguard their digital assets. By understanding the components of a feasibility study, engaging stakeholders, and evaluating technology solutions, businesses can develop a comprehensive security strategy. It is crucial for organizations to stay proactive in their approach to cyber security to effectively manage risks and adapt to the evolving threat landscape.
To support your journey in developing a robust cyber security framework, consider utilizing our Cyber Security Business Plan Template. Additionally, explore our insightful articles to further enhance your knowledge:
- Article 1: SWOT Analysis for Cyber Security: Strategies for Growth
- Article 2: Crafting a Business Plan for Your Cyber Security Firm: Step-by-Step Guide
- Article 3: Crafting a Financial Plan for Your Cyber Security Business: Essential Steps (+ Template)
- Article 4: Launching a Cyber Security Business: Complete Guide with Example
- Article 5: Crafting a Marketing Plan for Your Cyber Security Business (+ Example)
- Article 6: Building a Business Model Canvas for Cyber Security: A Comprehensive Guide
- Article 7: Customer Segments for Cyber Security Services: Who Are Your Ideal Clients?
- Article 8: Cyber Security Profitability: Maximizing Revenue
- Article 9: How Much Does It Cost to Start a Cyber Security Business?
- Article 10: How to Implement Effective Risk Management for Cyber Security?
- Article 11: What Are the Steps for a Successful Cyber Security Competition Study?
- Article 12: How to Address Legal Considerations in Cyber Security?
- Article 13: What Funding Options Are Available for Cyber Security?
- Article 14: Cyber Security Growth Strategies: Scaling Success Stories
FAQ Section
What is a cyber security feasibility study?
A cyber security feasibility study assesses the risks and benefits associated with implementing security measures within an organization, helping to identify vulnerabilities and develop effective strategies.
Why is stakeholder engagement essential in a feasibility study?
Involving stakeholders ensures a comprehensive view of the organization’s security needs, allowing for valuable insights into potential risks and existing security gaps.
What are the key components of a cyber security feasibility study?
Key components include risk assessment, technology evaluation, cost-benefit analysis, and developing an incident response plan.
How does a cost-benefit analysis help in decision-making?
A cost-benefit analysis compares the costs of implementing security measures against the potential financial losses from security breaches, aiding organizations in making informed decisions.
What role do compliance requirements play in a feasibility study?
Compliance requirements ensure that organizations adhere to legal standards, reducing the risk of penalties and enhancing overall security posture.
How often should a cyber security feasibility study be updated?
Regular updates are essential to ensure that security measures remain effective and relevant in the face of evolving cyber threats.
What are some common compliance regulations?
Common regulations include HIPAA for healthcare, PCI-DSS for payment industries, and GDPR for data protection in the EU.
How can employee training improve security?
Employee training raises awareness of potential threats and equips staff with the knowledge to respond effectively, thereby strengthening the organization’s overall security strategy.
What is the significance of an incident response plan?
An incident response plan outlines the steps to take during a security breach, helping to mitigate damage and restore operations quickly.
How does technology evaluation fit into a feasibility study?
Evaluating technology solutions ensures that organizations invest in security tools that align with their specific needs and budget, enhancing their overall security posture.